SAP GRC Access Control
Nowadays, new technologies development has recently brought equally dynamic development of companies and corporations. Enterprises strive to protect themselves against various threats and attacks. Threats are usually identified as external threats but actually there are also, hard to detect, internal threats. Meanwhile, employing many employees and using many systems, one should pay close attention to threats appearing within the organization. This type of risk is most often invisible, but its materialization can also have significant impact on the financial condition of the company.
To enable full control over the proces of conflict identification and resolution and to obtain compliance with various Acts e.g. the SOX (Sarbanes-Oxley), the management decides to implement the appropriate GRC class tool. One of such solutions is a dedicated SAP solution - SAP GRC Access Control.
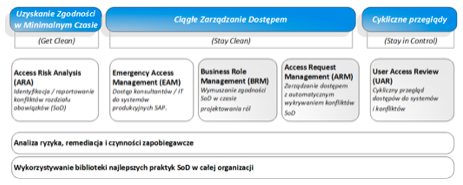
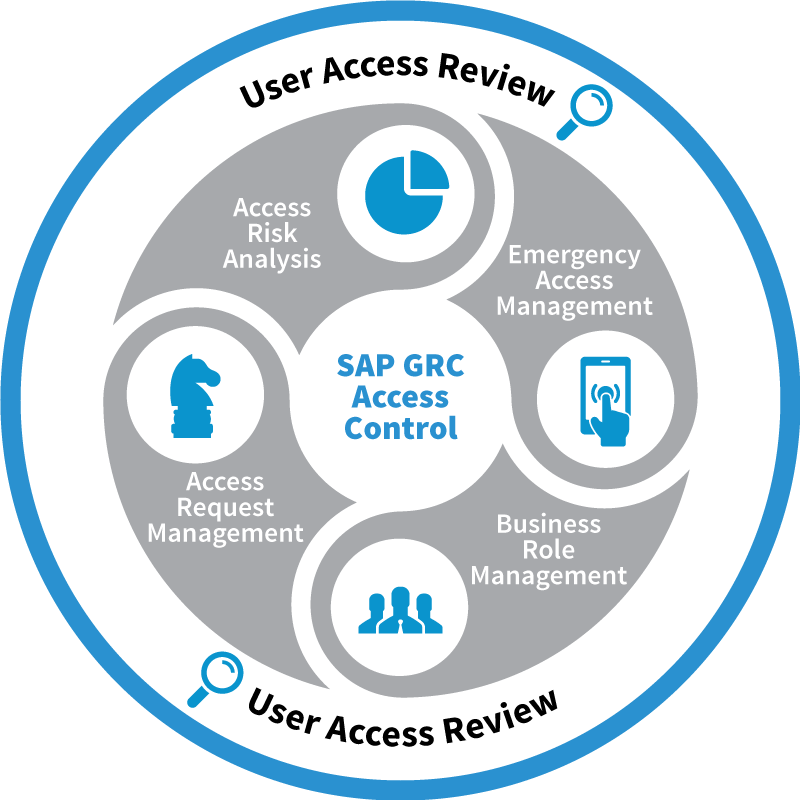
SAP GRC Access Control is a tool created to help organizations automate process of managing users access and to monitor SoD risk violations. It allows to personalize and customize processes related to users access management, business roles management, analysis and monitoring of the risk of segregation of duties (SoD), privileged / Firefighter access and periodical reviews of access to specific, individual requirements of each enterprise. SAP GRC Access Control is a software that allows you to manage this process in solutions from various developers (not only SAP, also Oracle or JDEdwards) and various systems e.g SAP HCM, ECC, BW or CRM).
SAP GRC Access Control consists of the following modules:
- Access Risk Analysis (ARA)
- Emergency Access Management (EAM)
- Bussiness Role Management (BRM)
- Access Request Management (ARM)
- User Access Review (UAR)
SAP GRC Access Control:
- Increasing the awareness of business by engaging them in the whole process of managing users and authorizations
- Automating the granting access process, which saves time spent on this type of activities until now (business / IT users can deal with other tasks) - documentation for the process stored on the SAP GRC side
- Automatic identification and mitigation of segregation of duties (SoD) risks in the system (also obtaining protection of sensitive functions in systems) - both in current and future (requested) user authorizations
- Possibility to prevent unintended errors due to broad access in backend systems
- Optimization of users work in the SAP system: harmonization of user access with their actual organizational responsibilities
- Providing the necessary information / audit documentation required during audits (internal / external)
- The ability to integrate with other applications and use on computers, tablets, smartphones thanks to SAP Fior
- Management dashboards presenting current security status in the area of access to systems
General Data Protection Regulation (GDPR)
To meet the requirements included in the GDPR, SAP GRC Access Control is a preventive tool enabling control of access at the authorization level. It addresses requirements in terms of emergency access, modifications of authorization on user and role level and reporting of access to data and risks related to SoD (Segregation of Duties).
SAP GRC Access Control – GDPR compliance:
- Restricting and monitoring access to personal / sensitive data
- Administrating and managing business roles by defining attributes of roles and approval paths for data that requires additional control
- Analyzing access risks to data and ensure continuous monitoring of access to data
- Comprehensive review and verification of data access for all users in the system
- Detailed monitoring of special accounts (Firefighter) used to work with sensitive data

ARA module – Access Risk Analysis
SAP GRC ARA is a dedicated tool for Segregation of Duties (SoD) analysis. This module has been designed to identify, analyze and solve all problems related to work safety and audit associated with laws and procedures compliance.
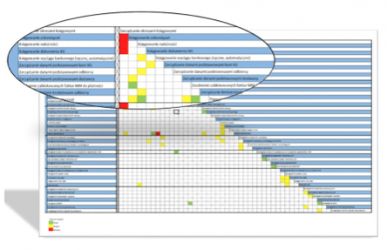
As part of the solution, a standard ruleset of segregation rules is available. It is based on best practices existing in business areas / processes, which can be tailored to the specificity of the client organization . It provides a comprehensive access risk management function for one or cross systems. It enables SoD risk identification, mitigation, reporting as well as performing simulation. Analyzes can be conducted collectively or per unit (based on dedicated Organizational Rules).
Reporting and analysis can be carried out on three levels: managerial (based on dashboards), business (business language understandable for business user) and technical (detailed information for IT / SAP consultants).
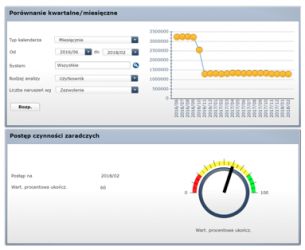
ARA module:
- SoD conflict matrix which reflects the current processes in the enterprise
- Detection of threats arising from too broad access and authorization of users
- Conducting risk analysis and generating SoD reports
- The possibility of implementing mitigating controls
- A simulation tool useful for making decisions about granting new access to users
EAM module – Emergency Access Management
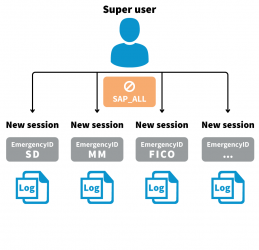
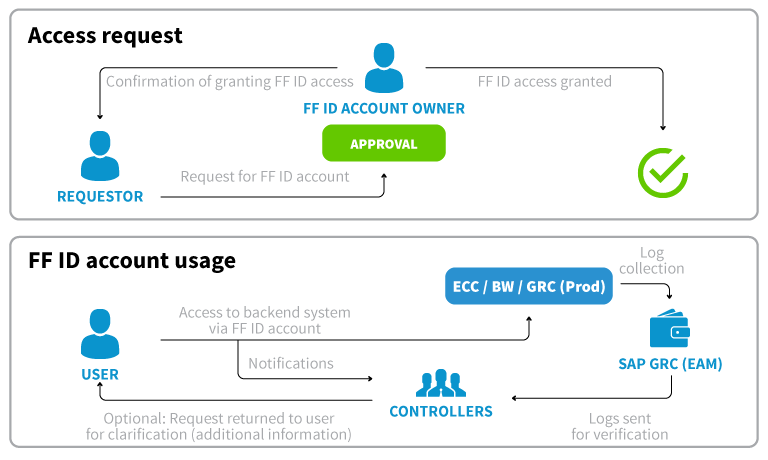
Monitoring emergency and privileged or IT consultants access to production systems is a key aspect from the perspective of business data security. This issue is very often reported by audit teams. Thanks to appropriately implemented SAP GRC EAM module, handling such events takes place through the use of Firefighter ID accounts. All actions taken while working on FF ID account are monitored and subject to review by appropriate users (Controllers) in the form of readable logs in the application.
Work with the EAM module is simple and intuitive. The consultant submit request for access to account with broad authorizations and applies for one of the available Firefighter ID accounts. Additionally, this process can be automated by introducing the appropriate Workflow within SAP GRC.
EAM module:
- Clear and transparent policy for managing special accounts (Firefighter ID)
- Full control over the activities performed on dedicated accounts in the system
- Reducing time required to obtain approval for privileged access to system
- Covering the most common audit recommendations regarding redundant access of consultants to production systems
BRM module – Business Role Management
The BRM module, being part of the SAP GRC Access Control solution, automates the process of managing cataloging and role definitions in a business-friendly way.
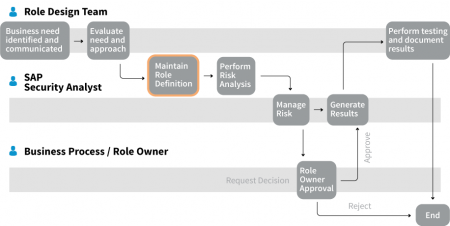
Thanks to usage of Workflow mechanisms, application allows full control and automation of the process of change management for roles (their designing, creation, defining, testing, as well as generation can take place from the SAP GRC level, without the need to log in backend systems).
Built-in integration with ARA module allows you to achieve synergy in role management: a proactive management process is aimed to eliminate segregation of duties conflicts (SoD conflicts) occurring within the role.
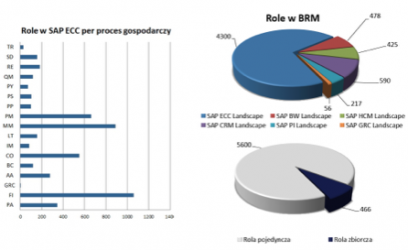
In addition, it enables comprehensive management of the organization's catalog of roles, in accordance with the best practices for many environments, various developers (not only SAP, eg Oracle, JDEdwards) and many systems (eg SAP HCM, ECC, BW or CRM). Simplified documentation for roles is stored in the system and presents their key parameters in a way that is understandable for both technical and business users.
BRM module:
- Provides organized and stored in one place business roles catalog
- Enables to eliminate SoD risks in roles
- It allows you to gain complete control over the change management process for roles
- Meets the requirements of external and internal audits in the role management process
- Enables the costs optimization of roles creation in various systems and environments (not only for SAP systems)
- Supports creation of composite / position roles
ARM module – Access Request Management
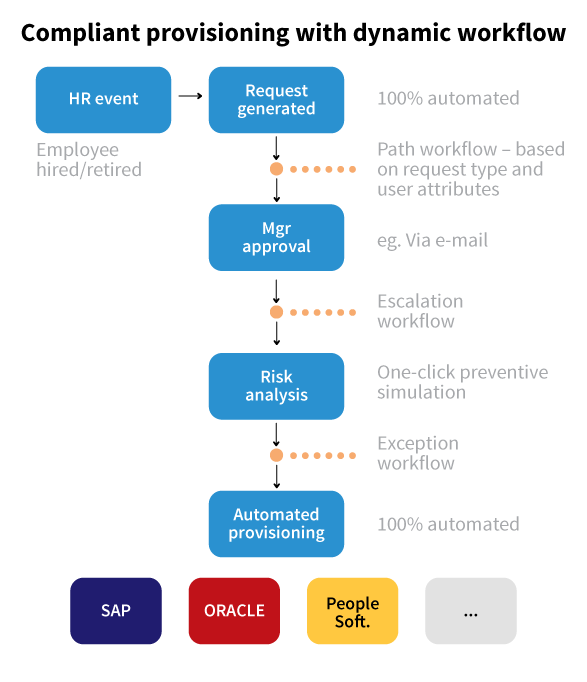
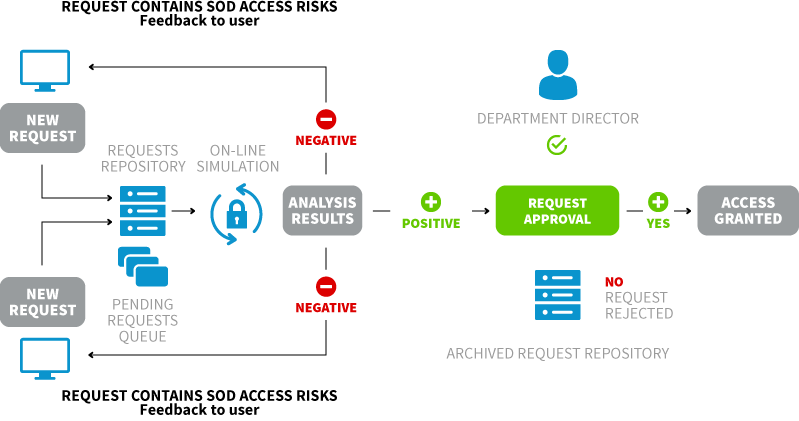
The SAP GRC ARM module enables the automation of user management processes and their authorizations based on requests. Thanks to a perspicuous interface it is possible to create request in easy way. Requests might concern e.g. granting or removing authorizations for yourself or another user. ARM module offers range of configurations. Allows to create separated approval paths for various requests types.
Tool enables to use the built-in risk analysis tool, which allows you to analyze in real time how the requested role will affect the state of SoD conflicts in the company and, if necessary, prevent new conflicts. All requests are archived and could be easily find using built-in search and reporting mechanisms.
ARM module:
- Automates of the authorizations management process
- Accelerates the process of granting access to users
- Allows an intuitive and understandable way of requesting access by all users
- Prevents new segregation of duties (SoD) conflicts by using risk analysis on the submitted requests
- Reduces working time of IT teams
- Adherences organization to security and audit requirements
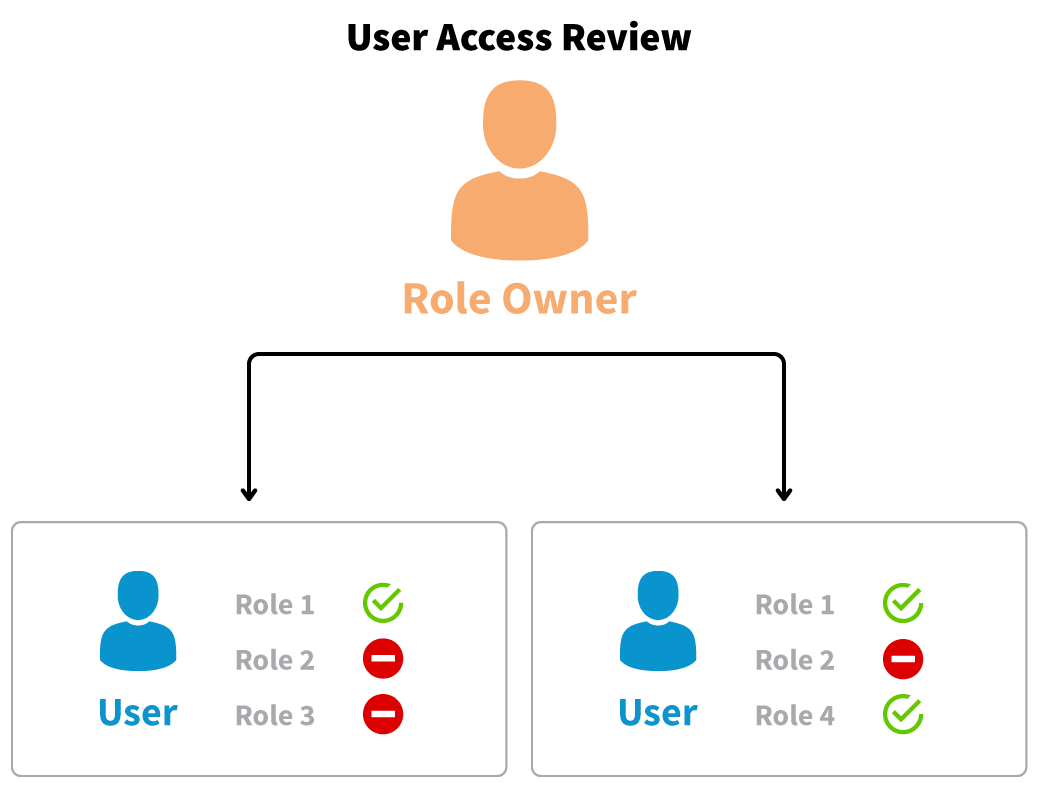
UAR module – User Access Review
SAP GRC UAR supports process of periodic reviews / re-certification of user authorizations. The purpose of the review is to harmonize user access in systems with employee responsibilities. In particual, during periodic user reviews redundant authorizations related to e.g remaining access after changing the position within the company, redundant roles can be removed from the user.
Thanks to dedicated Workflow mechanisms, system distributes requests with information about users and their authorizations in the system. Reviewers can make decisions about approving or removing roles from user. Decisions are automatically implemented in the systems.
UAR module:
- Automates process for periodic access review
- Continuous monitoring of the review process and decisions
- Automatic role removal, if needed
- Improves efficiency and transparency of the review process
- Audit trail and reports for supporting internal and external audits