SAP Security & Authorizations
S/4 Hana security conversion
When shifting from SAP ECC to S/4HANA, the fundamental architecture and data models are changed significantly. This can affect the way that user access and authorizations are handled in the new system. Therefore, it is important to review and update security and authorization during the S/4 Hana conversion process to ensure that they are aligned with the new system architecture and meet the organization's security requirements.
S/4HANA introduces new features and functionalities that require new authorizations to be defined. For example, new Fiori apps may need to be authorized for specific user roles. Therefore, it is important to review and update authorizations in the context of the new system capabilities. When converting to S/4HANA, here are some key considerations to keep in mind for security and authorization:
- Review and update user roles and authorizations: S/4HANA introduces new features and functionalities that require new authorizations to be defined. Therefore, it is important to review and update user roles and authorizations in the context of the new system capabilities. This will help ensure that users have the necessary access to perform their job functions, while minimizing the risk of unauthorized access.
- Review and update segregation of duties (SoD) controls: S/4HANA may introduce new business processes and transactions that require new SoD controls to be implemented. Therefore, it is important to review and update SoD controls in the context of the new system capabilities.
- Train users on new security and authorization features: Users may need to be trained on new security and authorization features in S/4HANA, such as the use of Fiori apps and new authorizations. It is important to ensure that users are aware of any changes to security and authorization settings and how they are affected by them.
The technical steps required to convert authorizations to S/4HANA may vary depending on the specific system landscape and business requirements. However, here are some general steps that can be taken during the conversion process:
- Prior to the conversion, it is important to perform a thorough analysis of the existing authorization concepts, roles, and profiles in the current system landscape. This analysis should identify any potential conflicts, redundancies, or inefficiencies in the existing authorization concepts. Review the transaction and corresponding custom programs usage to identify transactions no longer in used to be decommissioned from the system.
- Next evaluate the impact of S/4HANA on the existing authorization concepts, roles, and profiles. List roles and profiles that need to be adjusted in PFCG using expert mode.
- Based on the pre-conversion analysis and evaluation of S/4HANA impact, a detailed conversion plan should be developed. This plan should identify the roles and profiles that need to be adjusted, new authorizations that need to be defined, and any other changes that need to be made to align the existing authorization concepts with the new system architecture.
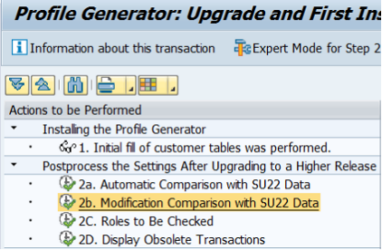
- Adjust roles and profiles – is S/4 Hana system this may involve removing redundancies, optimizing authorization assignments, and defining new roles and profiles. Before adjusting it is important to clean (update) content of SU25 transaction code and process steps 2a, 2b and 2c. Remember about updating technical definition of current SoD matrix to reflect changes coming from S/4 Hana security and authorization conversions.
- Define new authorization as S/4HANA introduces new features and functionalities that require new authorizations to be defined in current role model as well as in SoD matrix that safeguards your authorization concept.
- Test the new authorizations - once the new authorizations are defined, they should be thoroughly tested to ensure that they are working as intended and meet the business requirements. Ensure your sod reports are defining current sod risks, that includes changes coming from S/4 HANA conversion.
- Train users: Users should be trained on the new authorization concepts, roles, and profiles to ensure that they understand the changes and how they are affected by them
Contact us today to learn how our authorization conversion service can help your organization secure your S/4HANA environment. Our S/4 security and authorization conversion service helps organizations optimize their security settings and user access during the conversion process to S/4HANA. Our service includes a comprehensive pre-conversion analysis, evaluation of S/4HANA impact, development of a conversion plan, adjustment of roles and profiles, definition of new authorizations, testing, and user training. Our team has extensive experience in authorization conversion for S/4HANA and stays up-to-date on the latest security features and best practices. We understand that each organization's security requirements are unique, so we work closely with our clients to tailor our service to their specific needs. By using our service, organizations can ensure that their new system is secure and compliant with their security policies and regulations while users have the necessary access to perform their job functions. Contact us today to learn more about how our S/4 security and authorization conversion service can help your organization with its digital transformation .
Contact us today to learn how our authorization conversion service can help your organization secure your S/4HANA environment.
SAP Security
Security state assessment
An important element of the security state assessment is conducting an review and determining the current state of the application system security. The basic assessment is to verify the current user rights in the system are accurate and are reflecting employee job description. Such a process can take place for both business users as well as employees and IT contractors.
SAP configurable controls
SAP business process configurable controls drive the way business process risks are mitigated. There are numerous SAP configuration parameters that can be leverage as automated controls within standard SAP functionality. During initial system implementation project, different objectives have priorities, therefore many system parameters are not set for best practices. As a result, many typical business process risks are not covered, as controls components were not considered during system implementation blueprint phase. By optimizing SAP control, organization can reduce the risk of fraudulent activity, improve their effectiveness in monitoring business process risks.
Role and authorization redesign
Our company, based on audit background and the technical expertise of our consultants, offers services in the area of role redesign and authorization in the SAP system. We start from developing a business concept for user access roles, including SoD matrix (Segregation of Duties) requirements, to technical implementation of roles in SAP systems and support post-implementation. Our approach considers internal security and access risks requirements of the company and external regulations.

Periodic user access review
One of the key challenges, for security administrators, is to conduct periodic certification of user to role assignments. User authorization topic is very complex in SAP system, mainly due to massive number of roles and profiles assigned to user. This make periodic user access review difficult to execute, and sometime in extreme cases, this process is not carried at all. This process needs to support by external GRC tools (SAP GRC, smartGRC). Implementing a tool in this area can bring significant savings in the use of internal resources - both on the IT side preparing the review, as well as on the side of business departments, which are often responsible for verification of entitlements.
Support
Work on enhancing the SAP security and authorizations are processes that are directly influenced by audits, implementation of new functionalities, and changes in the legal environment. Adapting the organization to new requirements is an action requiring thorough domain knowledge and knowledge of best market practices.

As a response to these challenges, we support SAP security teams in the following areas:
- Role redesign and SAP authorization improvements - analysis and re-design of business role catalogs, technical role implementation, support in role tests, and post-implementation support.
- Support in the implementation of new requirements for the current SAP application roles architectures, for example: limiting access to personal data, implementation of segregation of duties (SoD), removal of critical access.
- Support for migration to S / 4HANA - adaptation of current role catalogs to the requirements of S / 4HANA, assessment and implementation of changes in segregation of responsibility (SoD) matrices.
- Implementation and support for GRC tools such as smartGRC, SAP GRC and others - implementation of additional functionalities and areas, error handling, user support.
- Construction and modification of segregation of duties (SoD) - analysis of the current situation and customer requirements, transaction mapping, implementation of changes in the matrix, tests.
- User support - ticket service, preparation of reports and analyzes, support during SoD analyzes, reviews and certification of permissions.
Cooperation forms
Loan staff - hire our SAP security consultants to support your security team in a full-time manner. In this cooperation model, the consultant works full-time under the client's management, performing the tasks assigned by him. Hiring consultants is an ideal proposition for companies that:
Project support - hire our team to support your SAP security challenge in role redesign project in a fixed fee agreement or more flexible time & material support.
